What is Configuration Management?
Configuration Management can be considered as a process that manages the configuration of IT infrastructures, like operating systems, network devices, applications, cloud services, and software. By enabling you to deliver better software faster, configuration management helps lay the foundation for DevOps. Configuration Management is important because it enables the ability to scale the infrastructure and software systems without having to correspondingly scale administrative staff to manage those systems.
Benefits of using configuration management tools
There are a lot of benefits of using configuration management tools and there are plenty of tools available in the market, each with their own set of features and capabilities, like Ansible, chef, puppet etc. Some of the benefits of using Configuration Management Tools include –
- Consistency of systems and software.
- When it is combined with automation, then it can improve efficiency as the manual configuration is quite slow and error-prone.
- We can run the configurations on multiple machines at the same time.
- It has centralized configuration means the configuration of various servers and devices are being done from the centralized server.
- Configuration management makes it easier to replicate environments with the exact same set of software and configurations.
- They support Idempotent behavior, which means keeping track of the state of resources in order to avoid repetitive tasks that got executed earlier.
What is Ansible, connectivity, and its architecture?
One of the most popular configuration management tools in the market is Ansible. Ansible is an open-source software provisioning, configuration management, and application-deployment tool.
Ansible provides following things:
- Orchestration
- Change Management
- Automation
- Provisioning System, Cloud
Automation is a set of task that a script executes. Multiple automation tools and scripts combine together to form a complete orchestration. Devops lifecycle is a complete orchestration i.e they work in an order.
Similarly, ansible works in orchestration.
Also, it helps in doing change management process which means everything needs to be documented. In ansible, playbooks will be written in a documented format.
Ansible Is Clean
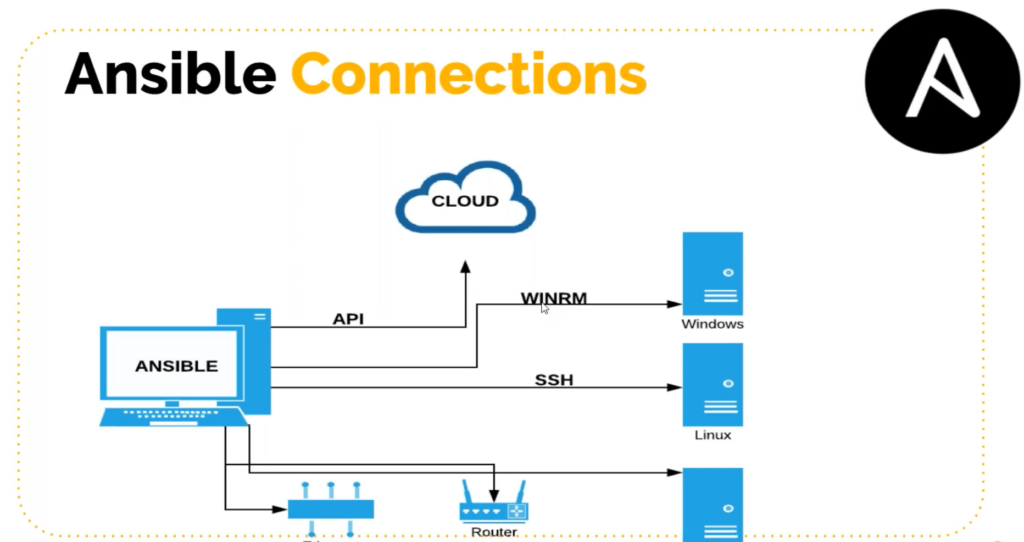
- No agents i.e target machines are access by ssh/winrm/API
- No Databases – Yaml, INI and texts
- No Complex upgrades – its very easy to install ansible, just a python library
- No residual software left behind
Note: Ansible can’t be installed on windows machine.
Language used in Ansible – YAML
Ansible Connections
Ansible Architecture
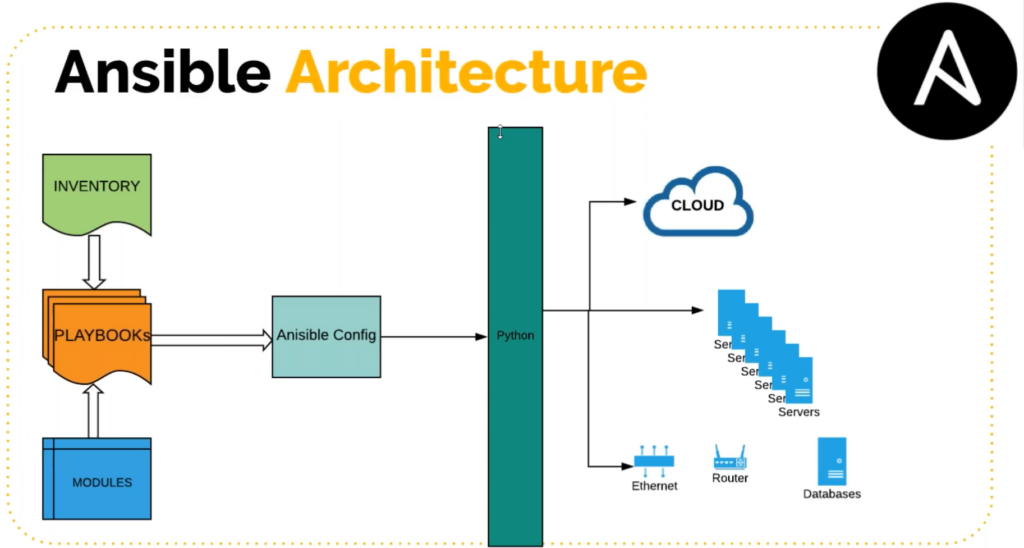
Please note that ansible is written in python. Through we would be writing playbook in YAML, but behind the scene it would be executed by python interpreter.
Ansible documentation:
https://docs.ansible.com/
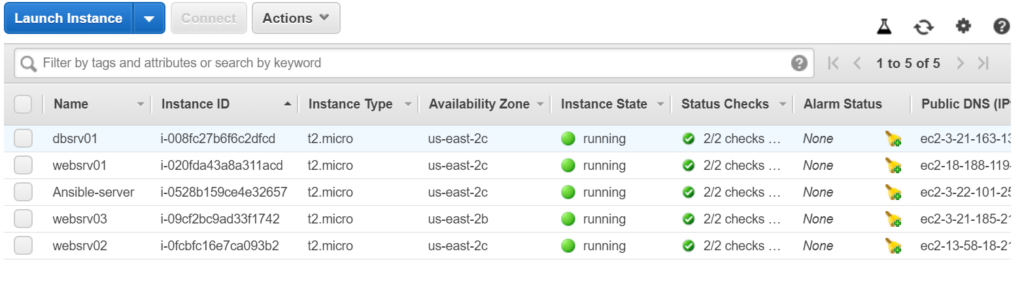
Let’s jump directly into practical. Now I will be creating 4 EC2 instances(1 ubuntu for Ansible installation, 1 Centos for DB connectivity and rest machines as web servers – 2 centOS and 1 Ubuntu)
Please note that ansible works with python 2.7 version. So make sure that the desired python version is installed on your machine, though version 2.7 would be installed by default as a dependency while installing ansible. However, agents machines can have any python version.
Let’s install ansible on Ubuntu machine now. We need to execute the below commands:
$ sudo apt update
$ sudo apt install software-properties-common
$ sudo apt-add-repository --yes --update ppa:ansible/ansible
$ sudo apt install ansible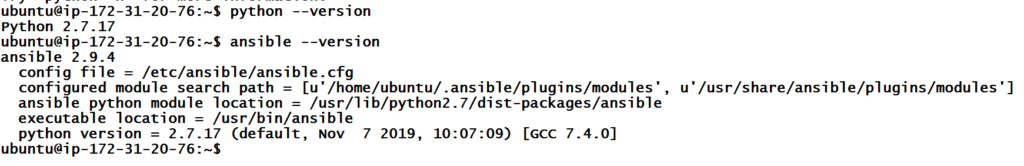
A few things to note here – We are using Ubuntu 18.04 version and Ubuntu 18 has Python 3 by default. We can see the version on the EC2 instance using the below command.
lsb_release -a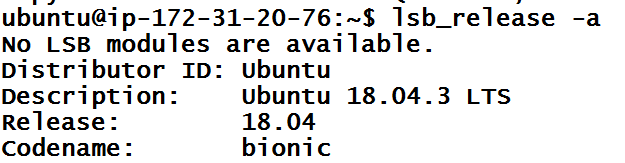
Ansible doesn’t use Python 3 on the local machine (i.e. the machine on which Ansible is installed) but the target machines can have python 3 installed.
As we know that from Ansible machine we are going to SSH to these web and DB servers, so we are now going to allow port 22 (which is the port no for SSH) for the Ansible machine. For this, we can either give the IP of Ansible EC2 instance or can give the security group of Ansible EC2 instance.
The second step is to setup a user on all the agent machine and give it sudoers permission and enable password authentication and restart the ssh service. We have to add a user on all web servers and DB server. For this, run the below commands.
sudo -i
useradd devops
passwd devops 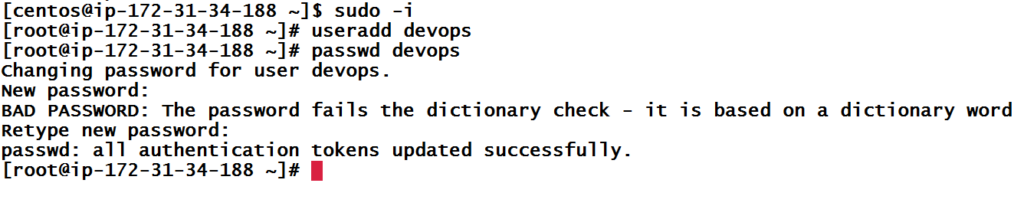
Once we are done with adding a user on all the web and DB servers, then we will give sudo privilege to the user so that we can SSH using this user and run root-level commands. visudo edits the sudoers file, which defines the users and groups with administrator rights. If we want to open sudoers file in vim then first we have to export the default editor which is nano to vim and this can be done with the below command.
export EDITOR=vim
visudo 
Last step in this is to enable password authentication. To enable SSH password authentication, you must SSH in as root to edit /etc/ssh/sshd_config file. Then, change the line
PasswordAuthentication no To
PasswordAuthentication yes
After making that change, restart the SSH service by running the following command as root:
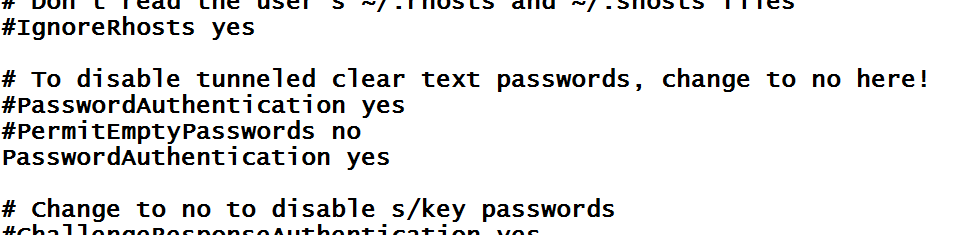
For ubuntu: service ssh restart
For centos: service sshd restart